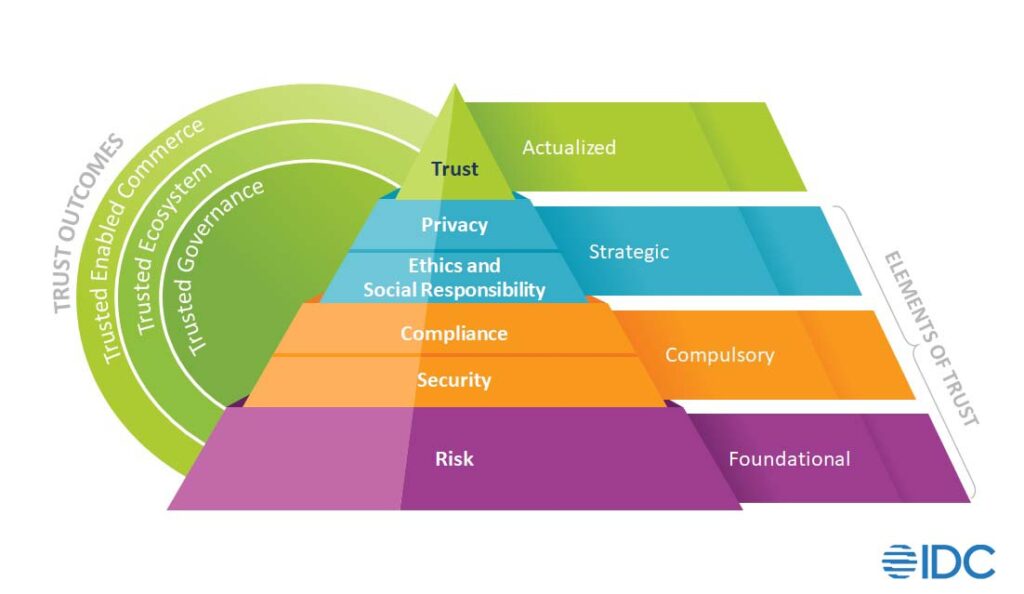
An organization’s management, both executives and board, need to view cybersecurity as not just a cost center but a way to enable the business to move forward at a faster pace, instead of slowing it down. Managing risk exposures with proactive cybersecurity tools and platforms should be a mindset, not a technology requiring investment. Since good risk management is the foundation of trust, organizations that do it well achieve the trust outcomes mentioned in our framework, benefiting themselves as well as partners and customers. Engendering trust within and outside an organization helps build loyalty; it only takes one lapse in the management of cyber-risk exposure to tear down what took time to build.
IDC’s expanded view of risk exposures includes:
- Unknown IT assets, including cloud assets, which are left unprotected by endpoint security tools
- Open ports that can be accessed by attackers from outside the organization
- End-of-life software because discovered issues are no longer being fixed
- Unsupported/antiquated devices that lack innate protections such as printers or IoT/OT assets
- Forgotten/unused/unauthorized applications, including SaaS applications, because the security team is not paying attention to vulnerability issues in that software, nor the data that is being stored in and transferred to or shared through that application, and nor misconfigurations in user access policies or password policies
- Remote desktop protocol (RDP) open to the internet
- Misconfigurations in cloud access policies
- Unknown domains/subdomains and forgotten subsidiaries
- Data in the cloud that is inadvertently exposed to cloud administrators through improper cryptographic key management
- Sensitive or confidential data that is stored improperly with a “trusted” third party
- Expired certificates because the browser cannot tell whether the website is authentic (If the users do connect, they cannot be assured that their communications with the website are secure and not through someone in the middle rerouting their traffic.)
- Unknown application programming interfaces (APIs) since APIs are being used to share information between applications (The APIs may be created by the organization or a third party to share information or integrate with partner applications.)
- Vulnerabilities in the code and applications the organization writes or assembles from open source
- Data exposed through lazy backup practices such as information stored in public folders during routine backup maintenance
- Hardcoded credentials/secrets such as API keys stored where they are accessible to attackers
The search and discovery of risk exposures needs to be continuous; there should be continuous scanning to enable continuous discovery and monitoring for continuous assessment and analysis of the data. Environments have grown complex with hybrid work, hybrid cloud, ephemeral workloads, and no traditional perimeter that can be protected by a firewall, so point-in-time data is not good enough. The days of monolithic software applications that are updated twice a year on a planned cadence have passed, replaced with a reality of a CI/CD-fueled microservices software architecture that experiences up to thousands of code drops daily. Today much of the code is open source as opposed to being developed internally.
In addition to new types of exposures, the sheer number of common vulnerabilities and exposures (CVEs) is growing as more are being identified and they are also being weaponized more quickly. Security teams need help to make sense of what is important.
Today, many point security products identify and report on these exposures including attack surface management (ASM), cloud workload protection, application security orchestration and correlation (ASOC), SaaS security, API security, certificate management, and vulnerability management. The data may come from various types of sensors: passive sensors, network scanners, internet scanners, agents, virtual scanners, secrets scanners, cloud connectors, APIs, and SaaS connectors. Each point product has its own reporting system and possible integrations with other platforms, making it harder, if not impossible, to correlate the data.
Ideally, all risk exposures should flow into a singular system, no matter how they are discovered, to ensure they can be comprehensively prioritized so the security team can direct their efforts accordingly and ensure it is maximizing cyber-risk reduction across the organization. The risk exposures need to be assessed, measured, and risk weighted based on a singular, homogeneous scoring criteria instead of individual security tools each measuring risk in its own unique fashion. Then the risk score is a comprehensive measure of cyber-risk that can then be integrated into the ultimate assessment — business risk.
Consolidation of point solutions provides a view of risk that, when combined with threat intelligence, provides a reality context weighted view. For example, a vulnerability that is recognized to have a known rootkit being leveraged within your market vertical and geography has a higher risk, all other things being equal, than one that does not. Other benefits may include a reduction of agents, simplicity in implementing automation, volume-based pricing available from a single vendor, and potential tool consolidation because fewer vendors require less time to manage.
In the meantime, some organizations could take even smaller steps towards better proactive cybersecurity by improving the percentage of assets scanned or scanning for vulnerabilities more frequently. According to IDC’s December 2022 Security Operations Center Survey, though device vulnerability management/scanning solutions are used by 82% of U.S. organizations with more than 500 employees, only 34% scan at least weekly. Only 26% report scanning 85% or more of their known IT assets. And that is the known assets; organizations may find around 30% more assets in their shadow IT that is unknown until an external scan is done.
In conclusion, cybersecurity risk management is not an end goal but a journey because the threat environment is continuously evolving, as is the organization. Being proactive means understanding the risk, determining what risk exposures are acceptable and remediating those that are not. Trust is an outcome of successful risk management.
- Thinking and management of risk exposures needs to be more broad than traditional vulnerability management.
- Visibility into the IT environment is key to proactive cybersecurity because a security team cannot protect the unknown, whether that is assets or applications.
- Proactive cybersecurity focuses on controlling the controllables, not just reacting to an attack.
- Recommended Actions:
- Monitor the environment continuously for previously unknown risk exposures because cyber attackers are doing the same.
- Investigate holistic risk exposure platforms in order to use standardized risk scoring to report on cyber risk from all parts of the IT environment.
- Remediate the risk exposures as soon as possible using automated workflows when feasible because attackers are moving faster than ever before.
- Share the risk data throughout the organization to make good cyber hygiene part of everyone’s job.
“With IT environments growing more complex and potential risk exposures more numerous, organizations need to think about using a holistic proactive cybersecurity management platform that brings all cyber-risk exposures to one place, so they are scored in the same manner. One management platform also simplifies prioritization and reporting.“
Michelle Abraham, research director, Security and Trust, IDC




