Organizations, especially during this current pandemic, are fighting to keep their IT environments secure, but this is becoming harder and harder to do. It is a challenge for businesses to keep up with the sophistication of attacks, as the adversaries are always one step ahead. Security teams are always looking for that one silver bullet to solve all their security problems, but we know that does not exist.
Shortages of cybersecurity professionals is not necessarily new news, but with that lack of a trained supply the price for acquiring that talent is going to add additional strains to a lot of firms that are struggling to emerge from challenging economic times. There is a huge dilemma for those organizations that want to have a robust security program and need a security operation center (SOC) but can’t afford to allocate space and invest in their own equipment and staff. For these many reasons engaging with a service provider is increasingly becoming an enticing option for many.
There continue to be several buzzwords that have explicitly entered the security services market. While some mean well and have value, others have become misleading. Terms such as machine learning (ML), artificial intelligence (AI), Endpoint detection and response (EDR), and big data analytics all seem to be overly used. Of course, all can’t be game changers alone without the right integration pieces. Additional services such as Managed Detection and Response (MDR) and SOC-as-a-Service (SOCaaS) bring even more confusion into an already confused market.
SOCaaS is not a new term; in fact, none of the terms listed above are brand new, but what is interesting is that they have all been intertwined in some way and used synonymously with one or the other. IDC has done an excellent job defining MSS and MDR, but there hasn’t been a clear definition around SOCaaS. No time like the present to clear some misconceptions around each of the various services.
Evolution of Managed Security Services
I thought it would be helpful to take us down a history lesson to understand how the MSS market began and has evolved over the past 5- 10 years. Let’s start with defining managed security services.
MSS 1.0
MSS has evolved into more since its introduction into the market well over ten years ago, with many providers being forced to offer more than just basic device hygiene. From IDC’s perspective, the first generation of MSS, classified as MSS 1.0, provided the management of traditional security devices such as firewalls, Intrusion detection and prevention systems. Alert management, guidance and recommendations are offered, but in-depth capabilities were lacking in MSS 1.0.
We see service providers offering these types of services, and that’s ok, but as time has progressed, we have moved up the stack to MSS 2.0, where service providers started offering advanced security capabilities.
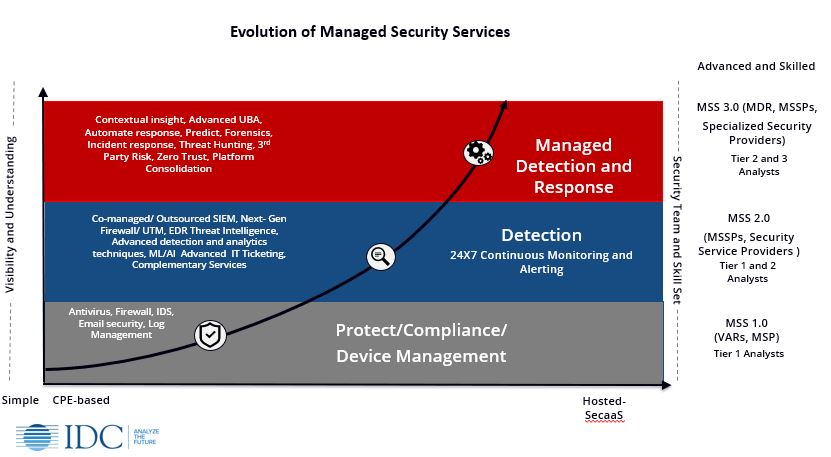
MSS 2.0
As the attack surface grew due to organizations undergoing Digital Transformation (DX), visibility became increasingly more important. The need to ingest more advanced capabilities became apparent, forcing service providers to accelerate their adoption of new security technologies such as machine learning (ML)/artificial intelligence (AI), automation and orchestration, and utilizing Security information and event management systems (SIEMs) to aggregate logs and compliance reporting.
Within this evolution it became evident that MSS was not only about managing devices, but also the data that these devices contain. The consulting arm grew in this era for many managed security service providers in offering investigation, forensics, and incident response as cyberattacks increasingly landed successfully.
So Where Does SOC-as-a-Service Fit in?
With organizations needing more help in advanced security functionality, especially around SIEM, organizations were forced to have either a security team in-house to do their own SIEM tuning, configurations, and updates or turn to a service provider that provided a managed SOC. A managed SOC is a central center that combines a team of security experts and 24X7X365 support of round the clock monitoring and management of security services. Organizations can outsource a set of security functionality to a SOC team, including those such as SIEM, vulnerability management, endpoint security, and other detection and response tools. Managed SOC models can be deployed in a co-managed or fully managed/outsourcing of security.
A managed SOC or SoC as a service, the “as a service” piece sometimes alludes to the fact that first of all, it’s a service, and second, it is a cloud-based platform and/or cloud-hosted or multitenant. That is not to say that the provider would not manage and monitor a customer’s premise equipment (CPE – Based) but the monitoring and response pieces can be done by a managed SOC or SoCaaS.
Where Are We Today?
MSS 3.0/MDR
Now bring in MSS 3.0, which is where MDR really starts to shine in this next generation of security operations. To have this complete lifecycle of services as stated, for example, in the NIST identify, protect, detect, respond, and recover framework, a new managed security service model was needed. MSS 3.0 is the evolutionary cycle that encompasses MDR. MDR is a subset of MSS which combines the tools, technologies, procedures, and methodologies used to provide full cybersecurity lifecycle capabilities for an organization.
Service providers can deploy MDR services utilizing a mixture of clients’ existing capabilities and cybersecurity partners supplied tools or services and private intellectual property. MDR is provided by a service provider’s well-trained cybersecurity staff in a 24x7x365 remote SOC. A managed SOC or SOCaaS also blends into this category as well.
Advice to the Buyer
IDC recognizes that there is a blurring occurring in the security services market, and the line between MSS, MDR, and SOCaaS can be quite confusing. In fact, my colleague also wrote a market perspective titled Blending Together/ Overlap of Consulting and MDR (US46232520) which discusses how consulting and MSS and MDR providers are overlapping and offering a wider array of services.
Organizations should steer away from getting caught up in all the different buzzwords occurring in the market. Instead, focus on what type of security assistance help you are looking to achieve. Are you looking for an extension to your IT team which includes 24X7X365 support across a variety a lifecycle of your cybersecurity needs? Think about what type of business outcome you are trying to achieve and what offerings will meet your IT requirements. It is also essential to think about the value in what the service provider brings to the table. What different levels of support are offered that will elevate your cybersecurity maturity?
In the end, focus on the people, process, and technology that will help you reach your longtime goals in improving your security and business needs. What else is happening in the worldwide security services market? Check out the 2021 Q1 on-demand IDC Security Services Team webinar to see latest trends, developments, and research:




