The CIA (confidentiality, integrity, and availability) triad is increasingly becoming the cornerstone for any organization’s security posture:
- Confidentiality refers to an organization’s efforts to keep their data private and secret. Typically, this involves ensuring that only authorized users and code users have access to specific data assets and that those who are unauthorized are actively prevented from obtaining access.
- Integrity is about ensuring that data and code data has not been tampered with or modified and, therefore, can be trusted. It is accurate, authentic, and reliable.
- Availability means that networks, systems, and applications running consistently and effectively while only allowing authorized users to have timely, reliable access to resources when they needed.
Findings from Interviews with CIOs/CISOs Regarding Privacy & Confidentiality
IDC interviewed several CIOs/CISOs from two highly regulated industries (healthcare/life sciences and finance) to understand key requirements, concerns, and challenges around securing datasets and maintaining regulatory compliance, and privacy. These interviews have helped uncover the fundamental reasons why Confidential Computing might be most beneficial for certain use cases and the challenges of adoption as well.
The interviews have highlighted the imminent need to protect data-in-use to preserve privacy and confidentiality to engender Trust when leveraging sensitive datasets in a multi-tenant or collaborative environment, especially in the public cloud.
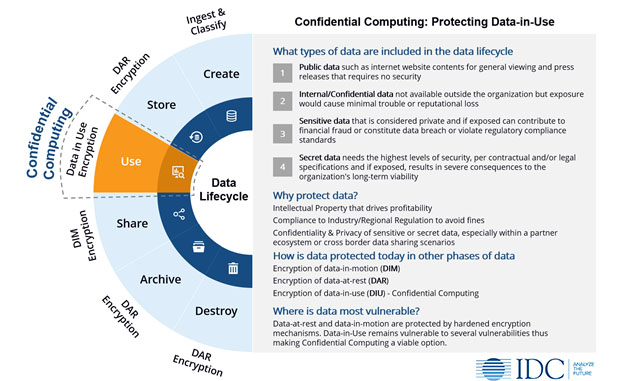
Why Protect Data in Use
During data-in-use state, it is imperative for the encrypted data to be decrypted to plain text for the application or code to consume/process it. On-premises infrastructure deployments address certain types of risk and security of sensitive data. Because on-premises deployments have been the norm for decades, industries and regulators have built a robust set of practices and requirements around data controls that include hardware level certifications, physical custody of devices, physical access controls, and security hardening recommendations.
The success of these practices and regulations has been variable, as many data loss events have nonetheless occurred, even in the most highly regulated industries. Highly regulated industries in particular face the serious risk of inadvertent access to and/or loss or breach of sensitive data due to an expanded ecosystem of (hardware/software) suppliers as well as lack of full visibility and control of the infrastructure/application stack in the public cloud environment.
We must understand that protecting data, code and IP depends on the threat model of a company – as in who or what they are protecting against, and what countermeasures are in place when on-prem.
The main thing to keep in mind is that, while adopting public cloud, the key concern is not whether the cloud provider would maliciously steal its customers sensitive data or intellectual property (IP). Rather the concern is protection from that rogue administrator, subpoenas, and being caught up in a breach targeted at cloud providers that do not necessarily target an individual organization.
More recently, Confidential Computing (see figure below) has created a buzz in the industry with a promise that it will enable customers to achieve a higher degree of security, confidentiality and privacy controls over its data and operational workloads through hardware-level security. Public cloud providers have brought to market services that are built on this concept. In addition to discussing this technology, this paper will address services made available by Alibaba, Amazon Web Services, Google, IBM, and Microsoft.
Confidential Computing
IDC defines confidential computing as a mechanism that protects data-in-use at the hardware level, thus offering highest level of technical assurance for security, privacy, and regulatory compliance in a multi-tenant, geo-dispersed or collaborative environment. The isolation and sandboxing techniques are designed to give the data owner (also known as controller) complete authority over its data and ensure that only authorized code authorized code accesses this data.
How Does Confidential Computing Work?
Confidential Computing is designed to provide security through the lowest layers of hardware thus minimizing the list of “trusted” parties, which can include operating system, device drivers, ecosystem partners, administrators, etc. This therefore reduces the risk of data exposure throughout the system lifecycle. This provides security guarantees for execution of code and protection of data-in-use within that trusted and isolated environment. Confidential Computing leverages hardware-based Trusted Execution Environment (TEE) that provides technical assurances in three main areas: technical assurances in three main areas:
- Data confidentiality. Confidential Computing protects data-in-use within the TEE by restricting unauthorized entities from viewing it. This provides technical assurances that the ecosystem of public cloud services and component/software partners do not have access to the customer datasets and therefore are protected from potential data exposure while responding to subpoena requests from legal entities or a third party.
- Data and Code integrity. Confidential Computing prevents unauthorized entities from altering data-in-use (when it is being processed) or code by any entity outside the TEE. This technology also provides code integrity which means that the code in the TEE cannot be replaced or modified by unauthorized entities.
- Data security. Confidential Computing provides a smaller attack surface and more security of data-in-use due to a tightened hardware-based root of trust. Essentially, this technology attempts to protects against the several types of vulnerabilities such as insider threats, firmware compromise, etc.
IDC Expands its Coverage of Confidential Computing
As the lead for Future of Trust research practice, I invite you to share your thoughts on this topic and access research on Confidential Computing
The Future of Trust research agenda is packed with thought provoking themes in 2021. Watch out for key upcoming research in the coming months:
- The Power of Trust: Measuring ROI
- Trust Centers: Committing to Transparency, Accountability & Good Governance
If you would like to learn more about the Future of Trust or IDC’s other “Future of X” practices, visit our website at https://www.idc.com/FoX




