Increased cybersecurity budgets that CISOs utilized to secure to the best of their abilities the almost overnight move to a work-from-home new norm during COVID-19 has caught the attention of the Board. Like any other significant budget expenditure that an organization spends on to fulfill its core mission, the capabilities and performance of the cybersecurity team, if not previously discussed, should now be a regular agenda item.
For some, this is where you cue the deer in the headlight memes. It’s ok. I’ve got the cheat sheet of items to add to the agenda that Board members can probably relate to. The Board’s role as the trusted advisor and corporate overseer is just as applicable to cybersecurity as it is to new product launches from marketing.
In no particular order of importance, here are 5 items to consider as the world starts to send people back to the office:
1. Cybersecurity Needs to Stop Being the Department of “No”
CISOs have a tough job. They are always just one missed step away from a headline-grabbing news item broadcasting to the entire world how their organization has become the latest victim of the cyber criminals and/or a nation-state sponsored latest attack. The knee-jerk reaction of anything that changes the delicate balance of relative cyber safety with an increase of the risk surface is to scream NO!
This is where the culture-setting attributes that the Board and the C suite set can help to refocus the CISO’s department. Their capability of shifting from a ‘No’, to a ‘Let’s figure out how to do this safely’ response can occur as they are brought into the discussion around strategic initiatives early rather than at the tail end. The days of making strategic decisions w/o seeking the input of security should be in the distant past. Regular interactions with the Board and the rest of the C Suite will allow CISOs to know that their input is valued, and they have trusted partners in the board room.
2. Physical Security Matters
As offices start to slowly fill up with mask-wearing people in the hallways, it may become more difficult to ascertain who is an employee or contractor from other people who may not have a justifiable reason for being in the office. If we can recognize this reality, then it is safe to assume that cyber criminals may try to take advantage of security protocols that have not been exercised or tested in a very long time to physically connect to the desktop computer in the corner cubicle that has been turned off for a year with no recent security patches applied.
This is a relatively high risk, low cost area of attention that security, facilities, and HR teams can team up on to make the necessary educational and structural changes to ensure everyone’s physical and cyber safety is protected.
3. The Future is Software. Hug a Programmer
If there is one item that came out of the SolarWinds cyberattack, it should be that the security of the applications that are driving the digital transformations (DX), and the security tools that help to secure this digital landscape, is written by programmers that utilize a mix of their own proprietary coding, open-source code, and other 3rd party applications. Any or all of these ingredients are fraught with the possibility of introducing vulnerabilities into the cloud-based apps and containers that are the part of DX organizations.
Addressing some of these security risks is aided if your development teams have already transitioned from a DevOps team structure, to one that incorporates a security by design methodology that is associated with a DevSecOps team structure. This does not offload secure design principles from the developers, but instead shifts secure coding principles, controls and processes into the agile sprints that make up modern development teams. Securing your internal development offers by adopting a DevSecOps approach, as well as training these rock stars with secure coding principles will help to keep your organizations name out of the headlights.
4. Follow the Money
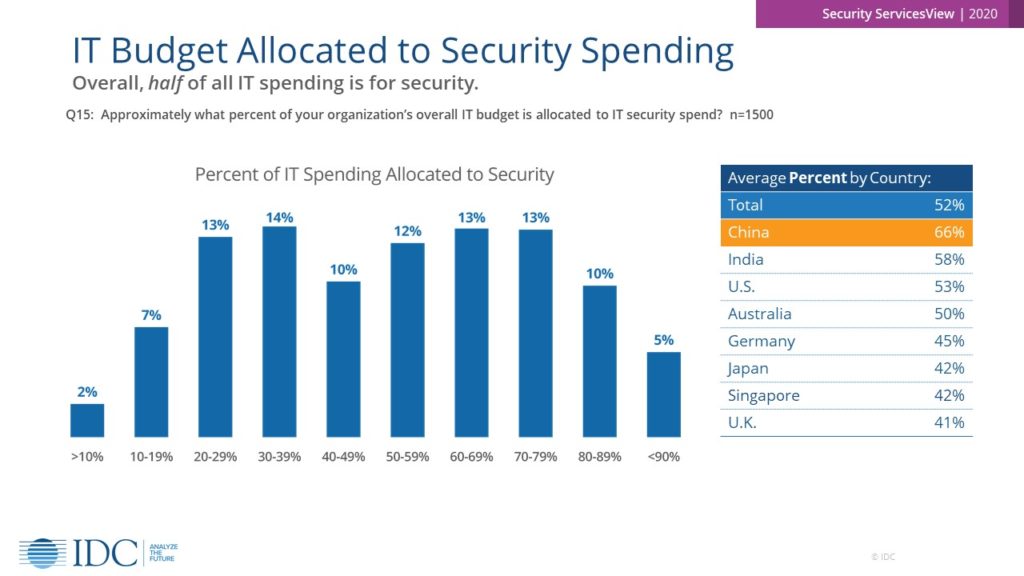
As noted in the IDC Security ServicesView Survey in November of 2020, organizations worldwide are reporting that security spending is taking up more of their IT budget. CEOs and presidents need to have at a minimum a dotted line between their box in the organizational chart, and that of the CISO. The assets that CISOs are entrusted with protecting require hard earned currency to stay safe, and honest conversations without the filter of a CIO or other C-suite seat getting in the middle are needed to make sure that the top of the org chart has a clear picture of the security posture that these dollars are spent on.
5. Risk
- This is where you start to read ahead and think that we are going to say how important it is for the CISO to manage and reduce risk. This is a false presumption. CISOs have a strong role to play in highlighting the potential increased risk that strategic changes in the organization does to the risk profile.
Security decisions today are not technical decisions; they are business decisions with the ultimate result being a changed risk profile. These decisions cannot occur in a vacuum, but instead require collaborative discussions from the Board, to the security operations center, to the various security services providers that provide the valued guidance that CISO’s need in these turbulent times.
Explore more findings from IDC’s Security ServicesView and learn how to best prioritize security services investments, value proposition messages, delivery mechanisms, and partnerships in the market:




