The C-Suite and other stakeholders are paying close attention to every dollar that traditional cost centers are spending. Cyber security is included as one of the departments that has seen increased scrutiny applied as their budgets have often seen increases even during a global pandemic. As Chief Information Security Officers (CISOs) look at the various needs within their critical department, they have to make some strategic decisions that they can defend and present to the board about where they are going to apply the budgets that fall under their control.
With so many news reports such as the recent Microsoft Exchange breaches and the repercussions of the Solarwinds hack still being felt, they are having to make decisions on the best way to protect their respective organizations from the cyber predators that seek to make their presence known in a big way.
Cybersecurity Investment Choices Need to be Made
One line of thought says that the best investment is to prevent incidents from occurring in the first place. It’s hard not to argue with this line of thought. It’s a philosophy that cybersecurity frameworks push, such as NIST’s 1st three goals of identify, protect and detect are geared towards. I know that if I identify healthy foods to consume, wear a helmet when out on my bike, and take part in regular health screenings, that the chances of my living a longer and healthier life increase.
If you were to talk to the leadership at Solarwinds or the Exchange architects at Microsoft, they would probably tell you that they were exercising the best security design principles that they had knowledge of at the time of their respective products releases, yet they were still hit. We could spend the entirety of this blog documenting recent attacks that have found their mark and inflicted their damage despite following recommended best practices. The sad truth is that the infosec community, and the makers of the products and services that we utilize to help protect us, will not always be able to protect us. My healthy eating, exercising, and health screenings can delay or minimize the effects of aging, but at some point my life here on this earth will end.
Does this mean that hard earned currency that is spent in protection is futile? Are all our firms destined to be just the latest victims in the modern-day version of a news reel? No…but it does mean that there needs to be a reality check done on the need for any firm with an internet connection and an asset worth protecting—that means everyone – needs to start practicing the art and science of incident readiness.
What is Incident Readiness?
The concept of practicing incident readiness often gets confused with incident response, but they are not synonymous with each other. IDC believes that incident readiness is what occurs when organizations prepare to act in the case of a security incident or attack by putting in place organized procedures to manage the effects of a security incident. The objective is to limit the damage of the security incident and reduce recovery time and costs. Incident readiness sets policies, plans and procedures to be followed in case of an incident.
There are numerous ways that firms can build up their incident readiness capabilities. The list is too big to be included in this blog, but some higher priority items to consider in building an incident readiness plan could include:
- Policies need to be established at the outset. If starting from scratch, don’t be afraid to reach out to a security services firm for guidance. This is an important step at a high level that will be leveraged as incident response plans and procedures are built based on the foundational principles that these policies formulate.
- Identify the potential participants that would need to be a part of any incident response engagement. This list includes personas that you may not necessarily identify as having any technology chops, but their respect areas of influence can be affected or influence the eventual outcome of a cyber incident. Areas like HR, PR & communications, legal, finance, and respective operations leaders would be resources that should be considered as well.
- Members of the above team should be considered as participants in a tabletop exercise. That 1st tabletop exercise could prove to be a bit longer than others, as the members of the incident response team learn about their roles and start to think about some of the decisions that would have to be made in the case of a real incident. Definitely an eye opening event!
- Assessments. Just to name a few, risk assessments, cyber security maturity assessments, and IT architecture assessments have to be performed. As digital transformation (DX) continues to progress throughout your organization, these assessments will be repeated on a regular cadence to make sure that your incident readiness capabilities are aligned to the strategic direction that your firm is heading in.
The above list just starts to scratch the surface, but the idea is to start putting not just the various technology teams that are traditionally associated with incident response and recovery or remediation efforts, but also the corollary teams that can help in media relations, compliance efforts, and business continuity and cyber resilience efforts.
Awareness of the Need for Help
Getting support for starting up a serious incident readiness program might be easier than one would suspect. In a recent IDC survey of respondents who were knowledgeable, influenced, or were responsible for security investments for their organization, the question was posed about how vulnerable their cloud architecture was to a reportable security breach. On a scale of 1 to 10, where 10 meant that they were extremely vulnerable, 77% were at a 7 or higher. The good news out of this that there is at least some recognition that there is a problem, and as we all know a problem is hard to handle until the recognition of the problem is made known.
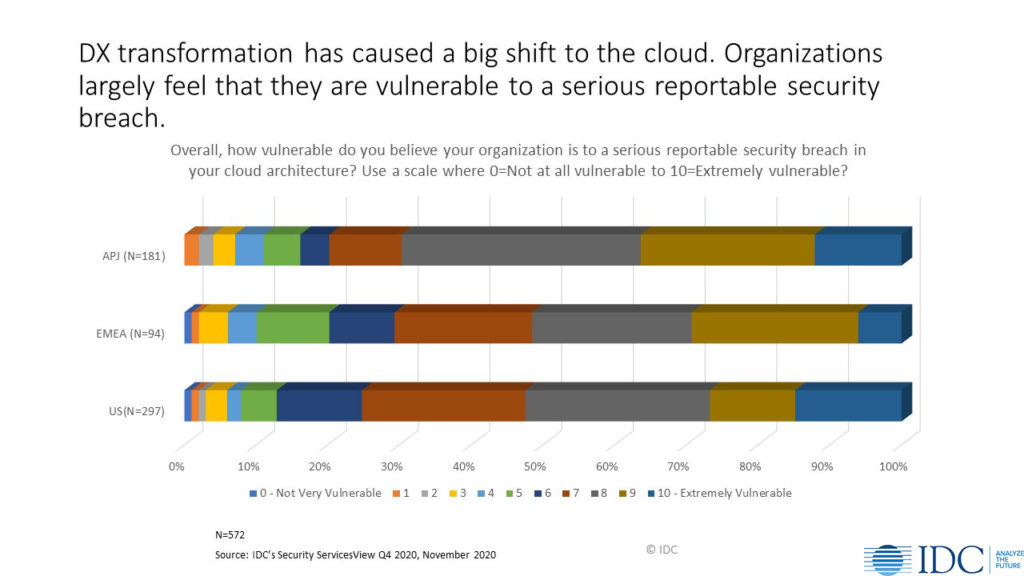
Being prepared to act decisively in the event of a security incident does not minimize the need to protect the organization from allowing the nation-state actors or other cyber criminal gangs from prying their evil craft. The incident response team should not become full time jobs for most members, so activities around preventing the need for these teams to get actively used is encouraged.
The post COVID-19 world will require businesses and other organizations to continuously evolve their business operations and their security capabilities that are aligned to protect the new ways that activities are performed. Knowing that your organization is prepared to act in the face of imminent threats should provide some peace in a not so peaceful world.
Want to explore the other areas of security services our team is focusing on this quarter? Check out our Security Services Market Update Webinar on demand now:




