For many Chief Information Security Officers (CISOs), the global pandemic has had its own unwanted “Quarantine 15” effect (similar to the “Freshman 15” we encounter in our first year at college) on the cyber health of the firms that they are pledged to protect. Long-fought-for gains that CISO’s have wrested from the C-suite and boards allowing for full-feature cyber programs to detect, prevent, and eradicate threats as needed are now under assault by budgetary hawks that are understandably looking for savings anywhere they can be found. These cost-cutting directives should come as no surprise as historically, technology-focused departments, which cybersecurity falls within, are often looked at to shoulder their fair share of budget cuts during times of economic distress.
While there has been greater recognition of the value and importance of good cyber hygiene and how these practices can lead to greater trust in a firms’ value to its stakeholders, these budget-cutting necessities are going to push CISOs to see what they can do to keep their businesses safe while cancelling or delaying upcoming engagements.
The iterative process of figuring out what and where to cut starts to churn through the CISOs brain. Can that firewall upgrade be delayed? What about that pen testing engagement; Is it really needed as part of that new CRM project that marketing has been clamoring for? That phishing testing and education project would really help to raise awareness of good email security practices, but maybe it is pushed out to the next fiscal quarter?
Eventually, at some point, cyber hygiene slips. Cyber fitness, just like physical fitness, will harm the host over time when it is not properly utilized. Human beings can see the damage of weight gains on a scale or in the mirror, but what can a CISO do to see the damage that reduced cyber fitness shows?
The temporary cracks that were left open when cybersecurity budgets were squeezed may have allowed some cyber attackers to find a landing spot. The advanced nature of many nation-state sponsored attacks will often allow these attacks to find a nice cozy spot to stay and practice their evil craft without being readily found.
Threat Hunting Defined
One of the tools in the proverbial cybersecurity toolbelt that CISOs deploy is that of a human-led threat hunting service. Threat hunting can mean many things to many people, depending on who is asked for the definition. IDC recognizes 3 types of threat hunting:
- Response threat hunting occurs when an indicator of compromise (IOC) is identified. Security analysts will seek to eradicate the identified malware, and then search for other possible incursions by the attacker and the associated malware.
- Targeted threat hunting is when hunts occur around the high-value assets of an organization.
- Proactive threat hunting is driven around a hypothetical analysis of the tactics, techniques, and procedures (TTPs) of a likely adversary, and hunting around a likely area of compromise.
Responsive threat hunts are the types that are not easily delayed or cancelled, because this type of threat hunt occurs due to a known IOC. It is not normally ignored or put off, even during times of economic distress.
The other two types of threat hunting are more proactive and will become even more important as firms need to actively seek out and eradicate prior attacks that may have landed during recent times of poor cyber hygiene. Just as human beings may have to pay the price for poor eating habits, CISOs will need to remind the C-Suite and board of directors that as their firms ramp up business activity coming out of the recession, cybersecurity threat hunting, though expensive will be a necessary expense item.
Even during pre-pandemic conditions, one of the common key performance indicators (KPIs) that security researchers discussed was the dreaded mean-time-to-detect (MTTD) number. This KPI measures how long attacks sit within an organization’s landscape before it is either detected, or in the case of a ransomware attack, it shows itself. A 2019 study by IBM Security and the Ponemon Institute showed the average time to detect a breach is 206 days, or 6.8 months. It would be nice to think that with the increased recognition of better tools and services to detect threats, this number would be going down, but most measures of this key KPI see it getting worse, rather than getting better.
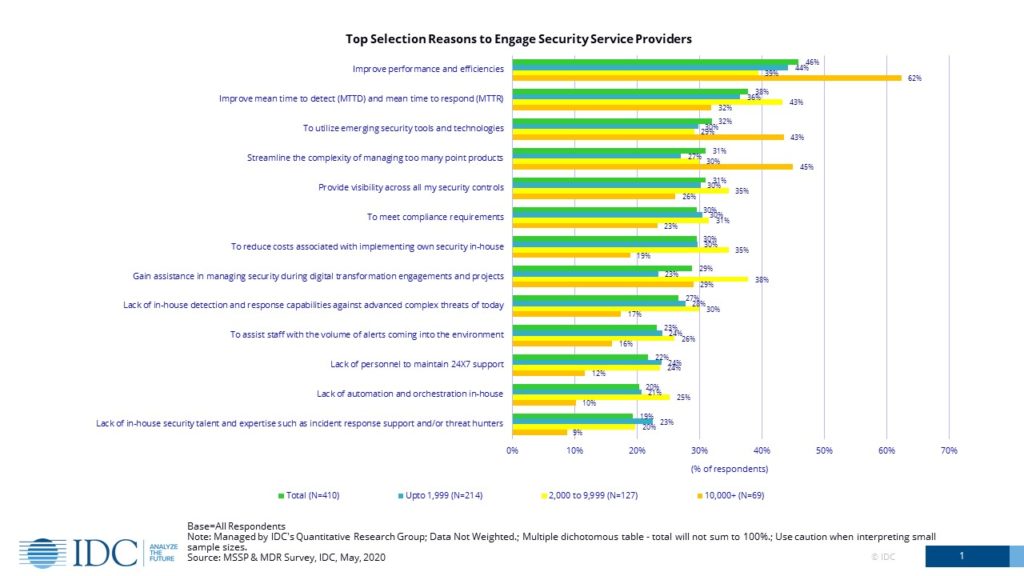
In a recent IDC MDR survey, nearly 40% of participants noted the need to engage security service providers in reducing the MTTD as well as the equally important mean-time-to-respond (MTTR) KPI’s. Delays or cancellations of these perceived ‘optional’ cybersecurity exercises with security service providers will allow the MTTD and MTTR numbers to continue to grow in the wrong direction.
Suggested Courses of Action
Cybersecurity service providers are often seen as that trusted advisor that CISO’s look to for guidance and additional capabilities in securing their organizations. Now that the initial shock phase of COVID-19 is over, it is time for these providers to step up to the plate and offer their clients that might have suffered from some recent cyber security lapses the financial flexibility that will allow their clients to engage in proactive threat hunting.
For CISOs that are worried about what may be lurking within their environments, this is the time to push the C-Suite for the monetary agility that will allow for their prized digital assets to be swept clean. Engage with your security services provider to quickly come up with a mutual plan on how you can cost effectively do some targeted threat hunts to secure your most-valued assets. If your services provider doesn’t offer threat hunting, look to engage one that is familiar with your industry and can be considered an extension of your current security operations team.
Every good weight loss journey starts with a recognition of the problem, and an action plan on how to achieve desired success. Re-establishing proper cyber hygiene requires a similar reality check that a sweep of the horizon by talented threat hunters is the best way to establish a clean cyber baseline.
Technology has proven to be critical to enabling businesses’ responses to the COVID-19 pandemic. Explore how organizations will leverage technology long-term as they move from crisis to recovery and journey to the next normal with IDC’s extensive COVID-19 research and advice.




